Are your comments infested with SEO spam for WordPress theme sites, pharmacies, or other spammy destinations? Is there a mysterious admin user in your WordPress admin panel? Have you noticed unknown PHP files or JavaScript code in your WordPress files? If so, your site may well be infected by WP-VCD.
What Is WP-VCD?
WP-VCD is malware. Malware is malicious software that is intended to damage, disable, or take control of systems. The system, in this case, is your website. The WP-VCD malware creates a hidden WordPress admin user and injects spam links throughout your content. It can even redirect pages to spam sites.
Malware can not only damage your site, but it can also take it offline. WP-VCD isn’t designed to take your site offline. But if your host finds the malware infection before you do, they will likely take your site offline as a preventative measure.
How Is WP-VCD Spread?
WordPress VCD malware is spread through WordPress themes and plugins. It is most commonly spread through “nulled,” or pirated, premium themes.
Premium WordPress themes often include code that prevents the theme from being installed on an unpaid site. If someone removes that protection and makes the theme downloadable for free, that is known as a “nulled” theme.
In the case of WP-VCD, when the nulled theme is activated, the malware immediately goes about injecting spam links. Once it’s active on your site, WP-VCD can also spread to WordPress installations on other domains in your cPanel account.
How Can I Tell If My Site Is Infected With WP-VCD?
The most obvious sign would be the presence of a WordPress admin user that is unfamiliar to you, or new links on your website (usually in comments) pointing to theme downloads, pharmaceutical, or other spammy sites.
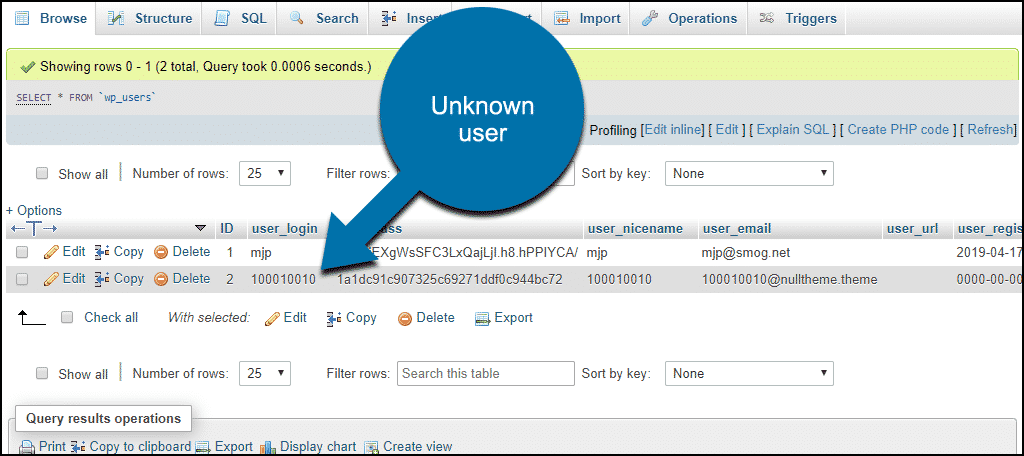
The admin user created by WP-VCD may be hidden, so you’ll have to check the database/" 91076 target="_blank">WordPress database to be sure.
Here we’re logged in to a database/" 91076 target="_blank">WordPress database with phpMyAdmin, and we can see an admin user that we didn’t create (and that we can’t see from the admin panel on the site).
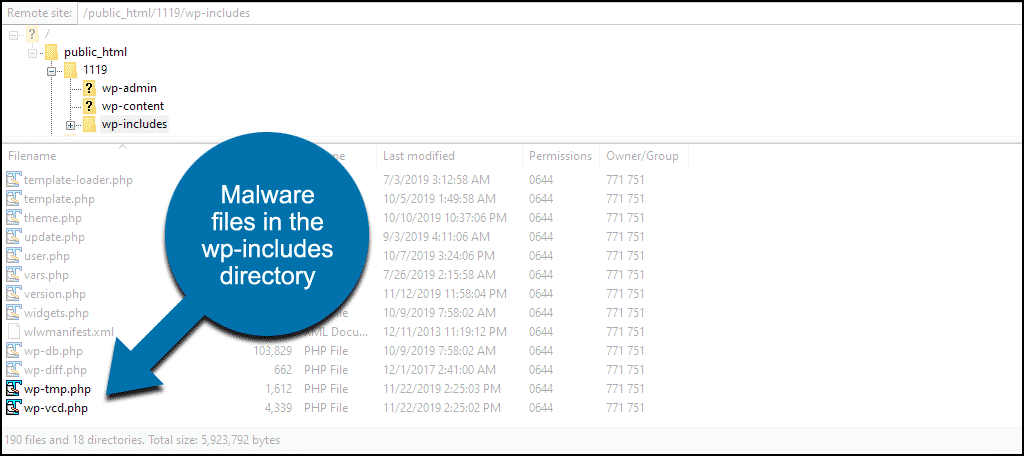
Next, look for files on your hosting account that are typically infected by WP-VCD.
These are the core wp-vcd malware files, and are commonly found in the /wp-includes directory:
- wp-vcd.php
- wp-tmp.php
These extra files may reside in your root /public_html/ (or the main /public_html/sub-folder/ if you have addon or sub-domains):
- class.wp.php
- admin.txt
- codexc.txt
- code1.php
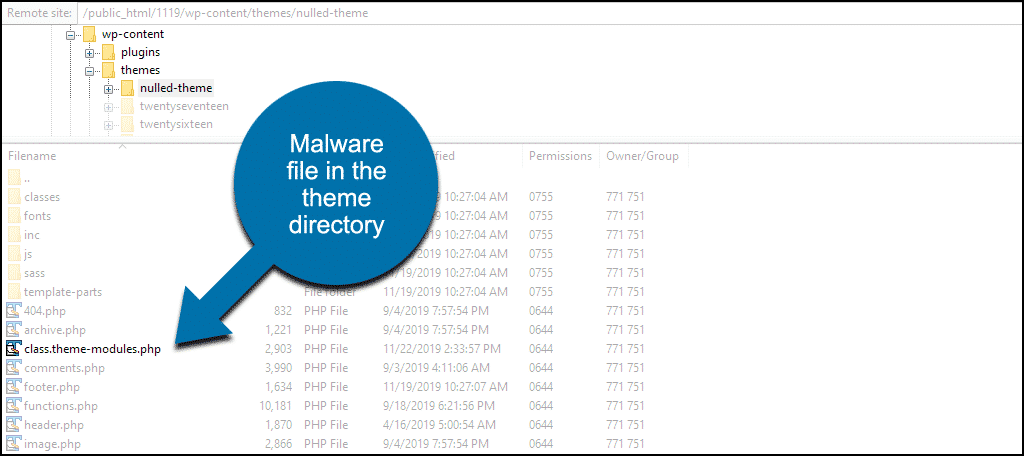
Finally, we’re going to look in the theme files. They are in /wp-content/themes/[theme name]/
In this example, the infected theme is in the /nulled-theme directory. So we go look in /wp-content/themes/nulled-theme for:
- class.theme-modules.php
Check all themes! Even themes that aren’t in use on your website. WP-VCD will attach itself to every theme it can find.
If you find some or all of these files, chances are that the theme (and probably every other theme in your WordPress installation) is infected.
How to Fix a Site Infected With WP-VCD
The best way to fix a WordPress site that has been infected by malware is to start over from scratch.
I know that sounds like the last thing you would want to do if your site is established and has a lot of posts or pages, but it’s the best way to be confident that your website is “clean”.
Starting from scratch doesn’t mean you have to lose all of your content. The good thing about malware like WP-VCD (not that anything about it is good, but, you know) is it doesn’t usually add code to the posts or pages in your database. So, it is possible to export only your posts and pages and import them into a new WordPress installation.
And it should go without saying, do not use a nulled theme or plugin in your new installation!
If You Still Want to Try to Clean a Site Infected With WP-VCD
To remove VP-VCD, the first step is to delete any nulled plugins if applicable, while making sure all others you are planning to keep are current and updated.
While you are updating your plugins, this is a good time to also completely remove any unused plugins from your WordPress installation. This dramatically reduces security risks for your site from plugins that are not updated by their author or have known vulnerabilities. This is something you should do periodically whether you’ve suffered a malware infection or not.
I’d strongly suggest deleting every theme, even the default ones from your WordPress Installation. Then, after removing the files below, reinstall the single theme you are planning on using from a reputable source. The repository of WordPress.org is usually a safe way to install themes.
Files to Look for that May Signify Infection
I could tell you to look for specific code in your theme’s functions.php file and delete it, but that’s ineffective and unnecessary. It’s ineffective because malware is always evolving. So new code could show up, and anything specific that I mention here becomes obsolete. Purging your theme directory is highly advisable.
Next, remember the files we looked for earlier? We’re going to delete those, but they should be deleted in this order to avoid reinfection:
- wp-includes/wp-vcd.php
- wp-includes/wp-tmp.php
You will also want to delete any file matching these below no matter where they are. (don’t worry if you can’t find any, that’s good):
- class.theme-modules.php
- class.wp.php
- admin.txt
- codexc.txt
- code1.php
Next, review or replace /wp-includes/post.php and ensure it does not reference the above files. If this file is infected and references wp-vcd.php or class.theme-modules.php, deleting it and replacing it with a clean version from the WordPress official downloads will ensure you have a clean file.
Finally, remove the rogue admin user that was added to your database from within PHPMyAdmin by deleting the row within the table. I would suggest taking a backup of your database before proceeding, just in case.
Please keep in mind that the WP-VCD malware is forever changing, and there could be leftover files or has adapted to common removal techniques. Have your web host perform a new malware scan after your cleaning to check for any leftover infections as a result of the WP-VCD infection.
How Can I Prevent My Site Being Infected With WP-VCD?
The best way to prevent a WP-VCD malware infection is to avoid using a nulled theme or plugin.
How do you do that?
- Don’t download themes from sketchy websites that advertise premium theme downloads for free.
- Don’t try to get around paying for a theme or plugin that you know charges a license fee.
- If you like a premium theme or plugin, pay the developer for a license.
These simple things will protect your website from things like WP-VCD, and it will also help support the third-party WordPress developer ecosystem that makes WordPress the powerhouse that it is.
You can avoid accidentally coming across a nulled theme by only downloading themes from reputable developers or marketplaces, or from WordPress.org. Legitimate WordPress theme marketplaces include Themeforest, Elegant Themes, StudioPress, MOJO Marketplace, CSSIgniter, and others.
Install a WordPress Security Plugin
Security plugins like Wordfence can identify many different kinds of malware and prevent you from installing them, or alert you to their presence. Most of them also perform dozens of other checks and can take steps to increase your WordPress site security.
And of course, there are a lot of things that you can do to enhance the security of your site.
Automatic Protection
While it pays to be aware of threats like WP-VCD, if you’re a GreenGeeks customer, you can rest easy knowing that your website is protected by our Real-Time Security Scanning. Utilizing a sophisticated file tracking system, Real-Time Security Scanning proactively identifies and scans changed files, finding known malware signatures.
So even if you unknowingly upload an infected file to your website, our system will recognize the threat and attempt to isolate the file(s) that contain malware. Real-Time Security Scanning will help you avoid the problems caused by WP-VCD and many other potentially destructive forms of malware.
If you’re a GreenGeeks customer and need further assistance in fixing an infected site, our team is experienced with WP-VCD and can help with cleanup or advise on your options. Feel free to contact us.
Have you ever had to clean up a malware infection? Do you use a WordPress security plugin?